Phishing Emails. What to look for to protect yourself, your team and your organization.
Phishing has long since been a go-to for the bad guys as an easy way to get malware on or access to victim computers. The trick for the bad guy / attacker is to make the email look like something legitimate and trigger some sort of fear response. The trick for the good guy / target is to be able to spot the scam, and that’s the point of this quick post. The email below is one that I just received that’s trying to get me to click on a link to confirm my email address. Let’s take a look.
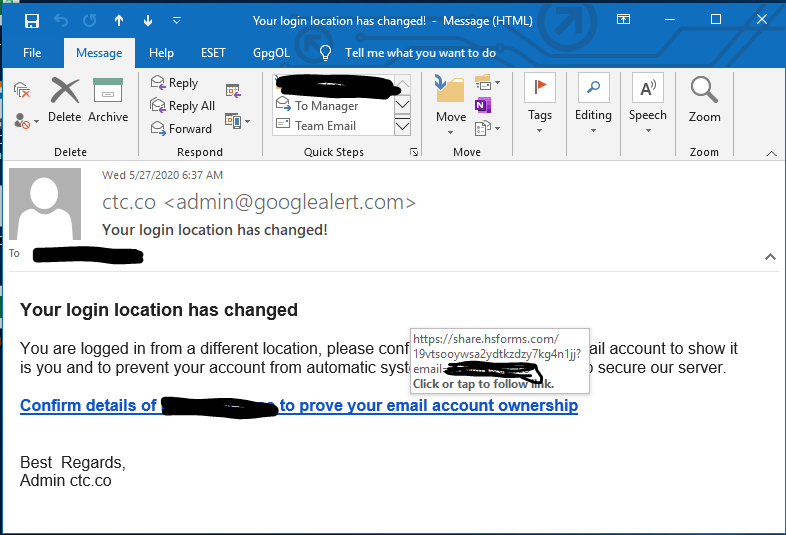
In the email above, the goal of the attacker is to get the target to click the link to ‘prove your email account ownership’. The email looks real enough. It claims to be from Google (admin@googlealert.com), it’s addressed to me, there’s no attachment and my SPAM filter didn’t catch anything. A deeper dive shows a few hints though that this isn’t legitimate.
- The email is from admin@googlealert.com. This looks like a Google address but the domain googlealert.com actually is not a Google property. We can check this at CentralOps.net and, though it doesn’t say who owns it (it just says GDPR Redacted), it does confirm that it’s NOT the same as most Google Properties. This is actually owned and hosted by someone named Pairdomains.com. Strike One.
- We can hover over the link (don’t click on it) and see where it actually goes. We would expect a link that we’d use to verify our Google account to go to a Google property but, instead, this one points to a share.hsforms.com domain. A quick look at share.hsforms.com shows that it’s a free online forms builder.
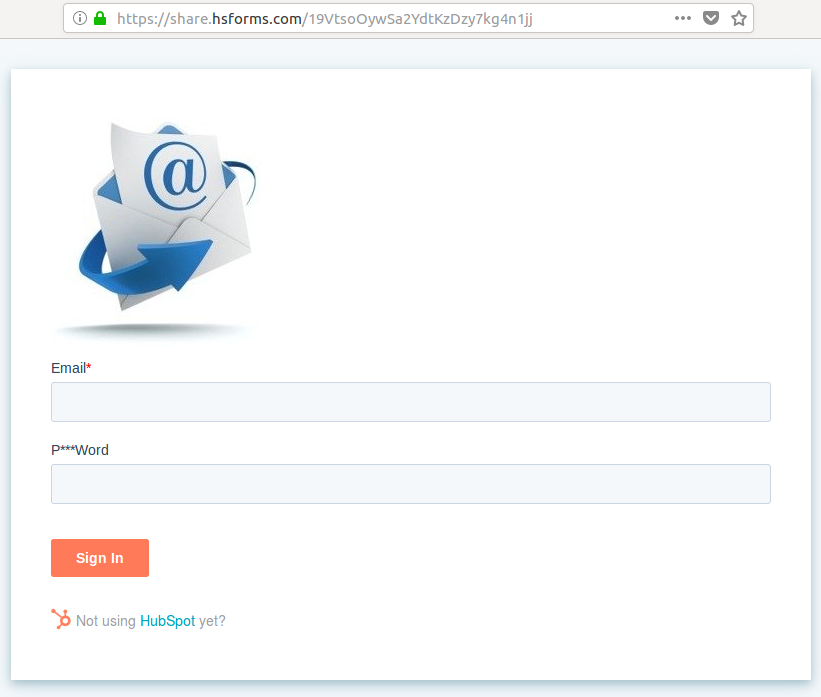
- If we do happen to click on the link, we get the page below prompting for our email address and password and, again, definitely not a Google property.
With more and more people working from home and losing the protection of their corporate firewalls and quick / immediate access to their peers for support, we’re seeing a spike in the number of social based attacks like phishing. If you believe that a member of your team may have fallen victim to an attacker or if you’d like to discuss how you’re currently protecting your remote workers (and your environment from them), we’d love an opportunity to earn your business.


