Please update your FortiGate
What is this about?
In February of this year, Fortinet disclosed multiple vulnerabilities in the FortiOS firmware, the operating system for their entire line of products. The vulnerability was highly publicized by Fortinet, The U.S. Cybersecurity and Infrastructure Security Agency (CISA), news outlets, message boards and on social media and we reached out directly to all of our MyIT Clients. The vulnerability is significant because it’s position in a network, often running on the Internet facing firewall protecting that network from Internet borne threats, means it’s exploitable from anywhere on the Internet and successful exploitation could give an attacker full access to a vulnerable device. It’s also important to note that state sponsored threat actors are known to favor (and target) these types of vulnerabilities.
What do I need to do?
If you are a Cyber Tech Cafe MyIT Customer, nothing, you’re up to date. If you are not a Cyber Tech Cafe MyIT Customer and you have Fortinet equipment (FortiGate firewalls, FortiSwitch switches, FortiAP access points, etc.) in your environment, verify with your IT Support Team that the FortiOS version on that device is up-to-date and not vulnerable to this vulnerability (a good list of what versions are and are not vulnerable is available from Rapid 7 here). If you do not have an IT Support team, we’d be happy to help.
Why this article?
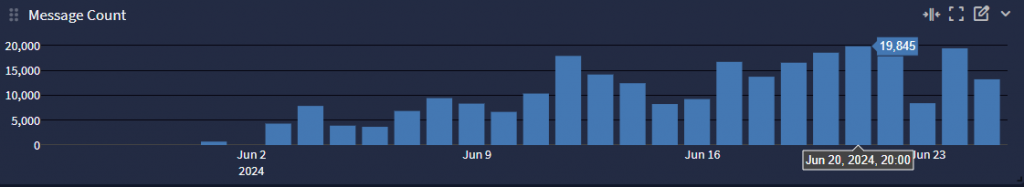
Four months after the disclosure and the updates to patch the vulnerability have been released, we are still finding Internet facing FortiGate firewalls with the vulnerable SSL VPN service available running woefully out-of-date versions of FortiOS including FortiOS 6.0x and even FortiOS 5.0.x making them easy prey for attack. We’re also seeing failed VPN Logins start to spike again, hitting over 19,800 failed logins on 20 June 2024, suggesting a renewed interest in this vulnerability.